본 게시물은 AI를 활용하여 논문 “Safeguarding Virtual Healthcare: A Novel Attacker- Centric Model for Data Security and Privacy”에 대한 주요 내용을 요약하고 분석한 결과입니다. 심층적인 정보는 원문 PDF를 직접 참고해 주시기 바랍니다.
📄 Original PDF: Download / View Fullscreen
영문 요약 (English Summary)
Safeguarding Virtual Healthcare: A Novel Attacker-Centric Model for Data Security and Privacy Suvineetha Herath , Haywood Gelman , John Hastings , Yong Wang The Beacom College of Computer and Cyber Sciences Dakota State University {suv
한글 요약 (Korean Summary)
가상 건강 관리 보호 : 데이터 보안 및 개인 정보를위한 새로운 공격자 중심 모델 Suvineetha Herath, Haywood Gelman, John Hastings, Yong Wang Beacom Computer and Cyber Sciences Dakota State University {SUV
주요 기술 용어 설명 (Key Technical Terms)
이 논문의 핵심 개념을 이해하는 데 도움이 될 수 있는 주요 기술 용어와 그 설명을 제공합니다. 각 용어 옆의 링크를 통해 관련 외부 자료를 검색해 보실 수 있습니다.
- Protected Health Information (PHI) [Wikipedia (Ko)] [Wikipedia (En)] [나무위키] [Google Scholar] [Nature] [ScienceDirect] [PubMed]
설명: (한글 설명 번역 실패 또는 없음)
(Original: Secure exchange of health information, ensuring that patient data is exchanged securely and in compliance with national and organizational standards [18] PHI encompasses any information related to an individual’ healthcare status or payment for healthcare services [19]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings [24] PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [20]. Security Frameworks for Securing Recent improvements in healthcare security technology can safeguard against both types of threats, emphasizing the importance of integrating technological solutions with organizational and human factors to enhance overall security settings. PHI violations have become increasingly prevalent virtualizing health-related data breaches. Safeguarding PHI has been a significant concern in virtual healthcare environments due to the risks posed by cybercriminals seeking unauthorized access [)
원문 발췌 및 번역 보기 (Excerpt & Translation)
원문 발췌 (English Original)
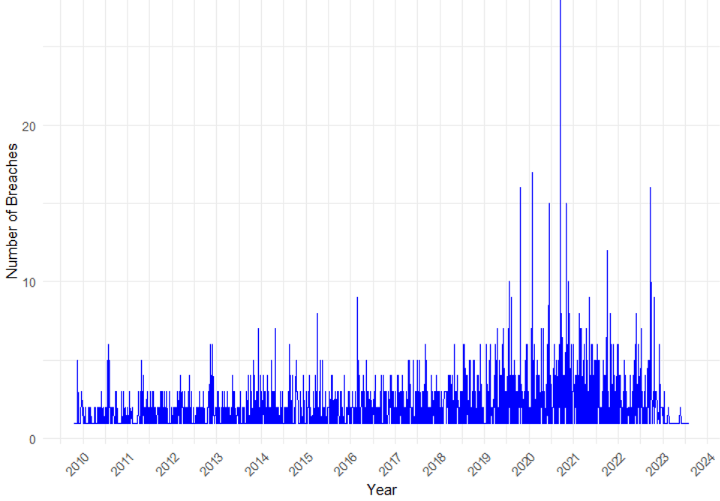
Safeguarding Virtual Healthcare: A Novel Attacker- Centric Model for Data Security and Privacy Suvineetha Herath , Haywood Gelman , John Hastings , Yong Wang The Beacom College of Computer and Cyber Sciences Dakota State University {suvineetha.herath,haywood.gelman}@trojans.dsu.edu, {john.hastings,yong.wang}@dsu.edu Abstract—The rapid growth of remote healthcare delivery has 13 years at an average cost to organizations of $10.93M introduced significant security and privacy risks to protected USD [10]. The rise in healthcare-related attacks over the health information (PHI). Analysis of a comprehensive healthcare previous three years isr validated by [11]. security breach dataset covering 2009-2023 reveals their signif- The growing reliance on virtual healthcare and the increas- icant prevalence and impact. This study investigates the root2024 causes of such security incidents and introduces the Attacker- ing interconnectivity of its systems have introduced vulnerabil- Centric Approach (ACA), a novel threat model tailored to ities that traditional threat models cannot handle. For example, protect PHI. ACA addresses limitations in existing threat models STRIDE-based models target vulnerabilities that compromise and regulatory frameworks by adopting a holistic attacker-Dec key security properties, including confidentiality, integrity, and focused perspective, examining threats from the viewpoint of cyber adversaries, their motivations, tactics, and potential attack18 availability (CIA). However, they do not adequately address the privacy harms that arise from healthcare data breaches. vectors. Leveraging established risk management frameworks, ACA provides a multi-layered approach to threat identification, This study investigates the root causes of security incidents risk assessment, and proactive mitigation strategies. A com- in virtual healthcare environments and develops the novel prehensive threat library classifies physical, third-party, exter- Attacker-Centric Approach (ACA) threat model, designed to nal, and internal threats. ACA’s iterative nature and feedback comprehensively safeguard PHI from evolving cyber threats. mechanisms enable continuous adaptation to emerging threats, ensuring sustained effectiveness. ACA allows healthcare providers The following critical research questions guide…
발췌문 번역 (Korean Translation)
가상 건강 관리 보호 : 데이터 보안 및 개인 정보를위한 새로운 공격자 중심 모델 Suvineetha Herath, Haywood Gelman, John Hastings, Yong Wang Beacom Computer and Cyber Sciences Dakota State University {Suvineetha. Herath, Haywood.gelman}@trojans.dsu.edu, {John.hastings, Yong.wang}@dsu.edu 초록 – 원격 의료 전달의 급속한 성장은 $ 10.93m의 조직에 대한 평균 비용으로 13 년 동안 보호 된 USD에 대한 상당한 보안 및 개인 정보 보호 위험을 도입했습니다 [10]. 건강 정보 (PHI)에 대한 의료 관련 공격의 증가. 이전 3 년간의 포괄적 인 건강 관리 분석은 [11]에 의해 검증되었습니다. 2009-2023을 다루는 보안 위반 데이터 세트는 가상 건강 관리에 대한 의존성과 증가하는 유병률과 영향에 대한 의미를 나타냅니다. 이 연구는 그러한 보안 사고의 Root2024 원인을 조사하고 시스템의 공격자 상호 연결성을 소개합니다. ACA (Vilnerabil-Centric 접근법)를 도입했습니다. 예를 들어, PHI를 보호하십시오. ACA는 기존 위협 모델의 한계를 해결합니다. 계약 기반 모델은 기밀성, 무결성 및 집중된 관점을 포함한 전체적인 공격자 -DEC 주요 보안 속성을 채택하여 사이버 적대, 동기, 전술 및 잠재적 공격 (CIA)의 위협을 검토함으로써 전체적인 공격자 -DEC 주요 보안 속성을 채택함으로써 타협 및 규제 프레임 워크를 목표로합니다. 그러나 의료 데이터 위반에서 발생하는 개인 정보 보호에 적절하게 다루지 않습니다. 벡터. 확립 된 위험 관리 프레임 워크를 활용하여 ACA는 위협 식별에 대한 다층 접근 방식을 제공하여 보안 사고 위험 평가의 근본 원인과 사전 완화 전략을 조사합니다. 가상 의료 환경에서의 컴파운드는 새로운 선제 적 위협 라이브러리를 개발하여 NAL을 위해 설계된 물리적, 타사, 엑스테르 공격자 중심 접근 (ACA) 위협 모델 및 내부 위협을 분류합니다. ACA의 반복적 인 특성과 피드백은 PHI가 진화하는 사이버 위협으로부터 종합적으로 보호합니다. 메커니즘은 새로운 위협에 지속적으로 적응하여 지속적인 효과를 보장합니다. ACA는 의료 서비스 제공 업체가 다음과 같은 중요한 연구 질문 안내서를 허용합니다 …
출처(Source): arXiv.org (또는 해당 논문의 원 출처)
답글 남기기